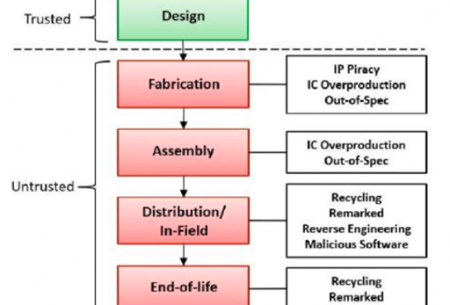
With the ubiquitous use of IoT devices in all walks of life, SoCs are subjected to various attacks to extract security assets throughout their lifecycle. Arm has an architected and evolving family of secure enclave implementations possessing a variety of security services and capabilities together that aim for attack mitigation and countermeasure techniques that are integrated into the overall secure SoC lifecycle. The design and integration of these secure enclaves need to achieve the highest assurance and certification of security, taking into consideration the intrinsic challenges of secure elements design and integration into the SoC lifecycle. To this end we perform a holistic study which comprises of two threads of activity: Vulnerability Analysis: We assess the security enclave’s (SE) ability to perform secure tests, SoC authentication among untrusted foundries, and OSAT environment. We also analyze the SE’s vulnerability to various threat scenarios such as information leakage, side channels, fault injection, etc. along with attacks such as man in the middle, impersonation, and more. Countermeasure Developments: We develop innovative solutions to ensure SoC authentication, in the field using AMI infrastructure and secure boot. We develop security policies to ensure proper implementation of SE and incorporate tamper resiliency for in-field.