

FICS Research Gains Sponsorship from FLDOE
Mark Tehranipoor, Ph.D., the Intel Charles E. Young Endowed Professor in Cybersecurity in ECE, Director of FICS, has received a $1.75M grant to establish a joint center between Embry-Riddle Aeronautical University and UF called the Center for Aerospace Resilience (CAR). The center’s mission is to investigate innovative technologies for resilience computing in space, soft-error protection, fault injection assessment of space devices and systems, digital twin for managing the avionics supply chain, security protocols for drones, and more.
Technology Highlight

Dr. Wally Rhines Now Chairs FICS Research’s Advisory Board
Dr. Walden ‘Wally” Rhines, son of the founding chair of the UF Department of Materials Science & Engineering (MSE) Dr. Frederick N. Rhines, is also is President and CEO of Cornami, Inc., a fabless software/semiconductor company focused on intelligent computing for fully homomorphic encryption and machine learning. He was previously CEO of Mentor Graphics for 25 years and Chairman of the Board for 17 years. During his tenure at Mentor, revenue nearly quadrupled and market value of the company increased 10X.
Prior to joining Mentor Graphics, Dr. Rhines was Executive Vice President, Semiconductor Group, responsible for Texas Instruments’ (TI) worldwide semiconductor business. During his 21 years at TI, he was President of the Data Systems Group, held numerous semiconductor executive management positions and was directly responsible for the creation and growth of the digital signal processing business which eventually comprised about 50% of TI’s total revenue.

2021 FICS Research TDC Registration Deadline 4/2/2021
This virtual event will focus on project demonstrations and sharing tools and solutions that our Institute’s faculty and students have been developing over the past several years. FICS Research TDC will also provide a unique opportunity for sponsors and collaborators to see the tangible outcomes of the work being done at FICS Research. This three-day event will provide technology demos focused on Hardware and System Security, that include CAD for SoC Security, Supply Chain Security, IoT Security, Malware Detection, Biometrics, Security Assessment, and more.
Registration deadline set for Friday, April 2nd, 2021
Register for free here.
Edaptive Computing Inc, Transition Center (ECI-TC) is Now
Hiring
Hardware/Digital Verification Engineer:
Job opportunity to become a member of the Edaptive Computing Inc. Development Team. Verification Engineer will model, simulate, and analyze complex IC and FPGA designs. Developer will perform research and implementation of advanced concepts, technologies, products, processes, and/or methods. Emphasis will be on Verilog and/or VHDL designs. Tasking will be focused on complex verification procedures in order to ensure Trust is maintained.
Hardware/Analog Verification Engineer:The candidate is expected to independently carry out hardware design and verification efforts as needed. The supporting activities for these responsibilities include verification process improvement through improved execution, documentation, or research. Additionally, the candidate will need to present work in formal/semi-formal presentations with confidence and understanding, and to communicate professionally with commercial and academic subcontractors.
For more info and to apply, click here.
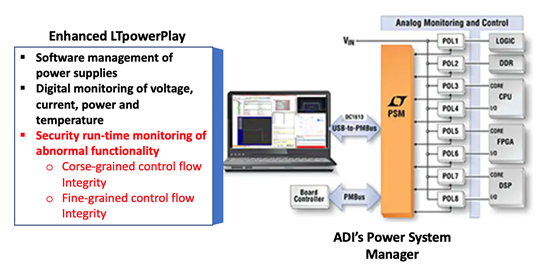
TrustGuard: Runtime Anomaly Detection in IoT Devices
Pis: Farimah Farahmandi, Jungmin Park, Mark Tehranipoor
With the advent of the Internet of Things (IoT), embedded devices, and networked high-performance computation platforms, many different types of cyberattacks such as malware, ransomware, distributed denial-of-service (DDoS), etc., have become a significant concern. All network-connected devices are susceptible to such cyber and hardware attacks. Since low-cost loT devices have limited resources, such as low processing power, and memory capability, deploying sophisticated defense mechanisms is extremely difficult and financially infeasible, which makes them attractive targets to adversaries. It is with no doubt that successful cyberattacks can lead to serious economic loss, infrastructural damage, or loss of life.
Thwarting the threats and vulnerabilities against cyberattacks requires lasting attention. In particular, runtime monitoring of computing devices is highly necessary to detect malware, unauthorized access, and illegitimate controls and applications. Such monitoring techniques can be either software-based and hardware-based. The software-based method mostly performs control-flow integrity (CFI) assessment which can monitor unexpected changes by a malicious code by analyzing the runtime control-flow graph (CFG). However, such software-based methods have disadvantages of performance degradation and unavailability to devices with resource-constrained architecture.
On the other hand, hardware-based methods usually use embedded and/or independent trusted hardware to observe the behavior of a program running on the device under a monitor. Hardware-based CFI architecture integrates hardware monitors into processor’s pipeline stages or hardware debug interface such as JTAG or scan chain is used to validate CFI at runtime. Hardware-based detection methods require a smaller overhead for resource and latency compared to the software-based counterparts. Recently, researchers have paid more attention to hardware-based methods that leverage side-channel leakages such as power consumption and EM. The side-channel information can also be leveraged for analyzing the status of a computing system at runtime.
To monitor firmware integrity in IoT edge devices by leveraging power side-channel information, FICS with the Analog Device Inc. team will research and develop ADI SW IP that enables ADI (Linear) Power Supplies to add security monitoring services for any embedded devices.This IP could monitor and detect if the edge device is compromised and running rogue firmware/software by analyzing the side channel signature in Figure 1.

Dr. Shigang Chen
Dr. Shigang Chen is a Professor with Department of Computer and Information Science and Engineering at University of Florida. His research interests include computer networks, Internet security, wireless communications, and distributed computing. He published more than 190 peer-reviewed journal/conference papers. He holds University of Florida Research Foundation (UFRF) Professorship and University of Florida Term Professorship from 2017 to 2020. He is a Fellow of IEEE, an ACM Distinguished Member, and a Distinguished Lecturer of IEEE Communication Society.
Research Interests:
Internet of Things, Cyber-physical systems, computer networks, Internet security, wireless communications, and distributed computing.

Major News

FICS Research Joins Coalition Against Stalkerware to support fight against digital violence
Gainesville, FL – 15 April 2021 – The Florida Institute for Cybersecurity Research (FICS Research) at the University of Florida announced today that it has joined forces with the Coalition Against Stalkerware to combat non-consensual tracking via digital devices and to provide technical approaches to support survivors of technology-enabled abuse and domestic violence.
Anti-counterfeit LDO Technology development and patent
Detecting counterfeit electronics could become easier.
Researchers at the University of Florida have invented a new way to detect recycled and counterfeit electronic parts that makes supply chains more secure, protects consumer safety and runs at almost zero cost.
Technology Highlights
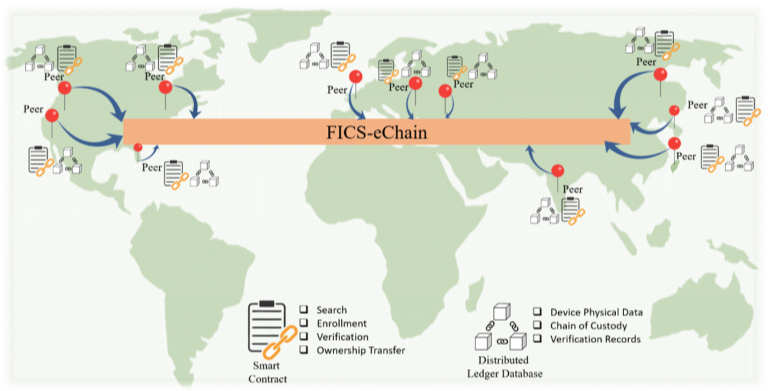
FICS-eChain: Enabling End-to-End Protection of Electronics Devices and Systems
In the modern digital era, counterfeit electronic devices and systems pose a severe threat to undisruptive service, users’ privacy as well as the national economy, and security. Adversaries can inject various counterfeit devices into the electronics supply chain due to its global and distributed nature and sheer operational complexities among numerous participants, which lacks distinct provenance, tracking, and traceability of the products from individual chips to large systems. Most importantly, traditional product verification schemes, usually provided by original component manufacturers, do not capture supply chain activities and associated risk factors at the granular phases, causing traceability and provenance analyses almost impossible. A team of researchers at the Florida Institute for Cybersecurity (FICS) Research have worked on building an infrastructure to provide a holistic solution to this problem. The infrastructure, called FICS-eChain, secure chain of provenance as devices and systems move worldwide from one entity to another and identify counterfeit devices across different supply chain phases.
Accolades

Mark M. Tehranipoor, Director, Professor, Intel Charles E. Young Preeminence Endowed Chair Professor
Congratulations to Dr. Tehranipoor who won HWCOE Teacher/Scholar of the Year.
We are extremely proud to announce that ECE Professor and UF FICS Director Mark M. Tehranipoor is the UF Wertheim 2020-21 Teacher/Scholar of the Year.

Lesly Galiana, Research Coordinator II
Congratulations to Lesly Galiana who won the HWCOE Staff Leadership Award and the 2021 ECE Excellence Award for Most Supportive Staff!
Huanyu Wang, Research Assistant
Huanyu Wang won 2nd place in the ComputerSociety TTTC’s E. J. McCluskey Doctoral Thesis Contest @ the 2021 IEEE VYS VLSI Test Symposium!
Title: CAD FRAMEWORKS FOR SECURITY ASSESSMENT AND PROTECTION OF ICS
AGAINST PHYSICAL ATTACKS.


Andrew Stern, Research Assistant
Andrew Stern won 3rd place in the ComputerSociety TTTC’s E. J. McCluskey Doctoral Thesis Contest @ the 2021 IEEE VYS VLSI Test Symposium!
Title: Secure Microelectronics from Design to Distribution.
Ulbert (Joey) Botero, Research Assistant
ECE PhD student Ulbert (Joey) Botero was recently awarded the 2020 Outstanding Paper at the Electronic Device Failure Analysis Society (EDFAS) Virtual Workshop, held December 7–9 of last year for his paper, “Automated Via Detection for PCB Reverse Engineering.”


Ana Covic, Research Assistant
Ana Covic Wins 2021 ECE Excellence Award in Graduate Student Service Award!

Major News

FICS Research Joins Coalition Against Stalkerware to support fight against digital violence
Gainesville, FL – 15 April 2021 – The Florida Institute for Cybersecurity Research (FICS Research) at the University of Florida announced today that it has joined forces with the Coalition Against Stalkerware to combat non-consensual tracking via digital devices and to provide technical approaches to support survivors of technology-enabled abuse and domestic violence.

Anti-counterfeit LDO Technology development and patent
Detecting counterfeit electronics could become easier.
Researchers at the University of Florida have invented a new way to detect recycled and counterfeit electronic parts that makes supply chains more secure, protects consumer safety and runs at almost zero cost.
Technology Highlight

FICS-eChain: Enabling End-to-End Protection of Electronics Devices and Systems
In the modern digital era, counterfeit electronic devices and systems pose a severe threat to undisruptive service, users’ privacy as well as the national economy, and security. Adversaries can inject various counterfeit devices into the electronics supply chain due to its global and distributed nature and sheer operational complexities among numerous participants, which lacks distinct provenance, tracking, and traceability of the products from individual chips to large systems. Most importantly, traditional product verification schemes, usually provided by original component manufacturers, do not capture supply chain activities and associated risk factors at the granular phases, causing traceability and provenance analyses almost impossible. A team of researchers at the Florida Institute for Cybersecurity (FICS) Research have worked on building an infrastructure to provide a holistic solution to this problem. The infrastructure, called FICS-eChain, secure chain of provenance as devices and systems move worldwide from one entity to another and identify counterfeit devices across different supply chain phases.
Accolades

Mark M. Tehranipoor, Director, Professor, Intel Charles E. Young Preeminence Endowed Chair Professor
Congratulations to Dr. Tehranipoor who won HWCOE Teacher/Scholar of the Year.
We are extremely proud to announce that ECE Professor and UF FICS Director Mark M. Tehranipoor is the UF Wertheim 2020-21 Teacher/Scholar of the Year.

Lesly Galiana, Research Coordinator II
Congratulations to Lesly Galiana who won the HWCOE Staff Leadership Award and the 2021 ECE Excellence Award for Most Supportive Staff!
Huanyu Wang, Research Assistant
Huanyu Wang won 2nd place in the ComputerSociety TTTC’s E. J. McCluskey Doctoral Thesis Contest @ the 2021 IEEE VYS VLSI Test Symposium!
Title: CAD FRAMEWORKS FOR SECURITY ASSESSMENT AND PROTECTION OF ICS
AGAINST PHYSICAL ATTACKS.


Andrew Stern, Research Assistant
Andrew Stern won 3rd place in the ComputerSociety TTTC’s E. J. McCluskey Doctoral Thesis Contest @ the 2021 IEEE VYS VLSI Test Symposium!
Title: Secure Microelectronics from Design to Distribution.
Ulbert (Joey) Botero, Research Assistant
ECE PhD student Ulbert (Joey) Botero was recently awarded the 2020 Outstanding Paper at the Electronic Device Failure Analysis Society (EDFAS) Virtual Workshop, held December 7–9 of last year for his paper, “Automated Via Detection for PCB Reverse Engineering.”


Ana Covic, Research Assistant
Ana Covic Wins 2021 ECE Excellence Award in Graduate Student Service Award!

Major News

Prof. Traynor Awarded $1.7 Million From Department of Homeland Security t0 Secure Cellular Networks
Patrick Traynor, Ph.D., the John H. and Mary Lou Dasburg Preeminent Chair in Engineering, was recently awarded a $1.7 million grant from the Department of Homeland Security (DHS) Science and Technology Directorate. The research and development project, titled “Deploying Defenses for Cellular Networks Using the AWARE Testbed,” will focus on securing mobile networks.

Supported by ONR ($900K), Prof. Navid Asadi Will Lead Development of SAIPA, a Secure Interposer Based Integration
SAIPA is a security-aware interposer design for heterogeneous packaging to investigate the vulnerabilities of interposer-based fabrication model and formulate various approaches to make use of the interposer features to ensure the security of the 2.5D fabrication model. Such an approach is of high importance to DOD because of the newly established zero trust assumption in building electronic devices and systems. SAIPA aims to assess the security vulnerabilities in an interposer-based split fabrication model and develop countermeasures to exponentially increase the complexity of solving the unknown connections through an interposer layer. SAIPA allows secure fabrication of electronic systems, while each die integrated in the 2.5 or 3D packaging may not necessarily be trusted. Further, DOD’s need to integrate a number of different dies into one package (digital, analog, memory, etc), makes SAIPA a necessity to establish security.

ARM/SRC Supports Prof. Farimah Farahmandi to Develop Secure and Extensible SoC Architecture
With the ubiquitous use of IoT devices in all walks of life, SoCs are subjected to various attacks to extract security assets throughout their lifecycle. Arm has an architected and evolving family of secure enclave implementations possessing a variety of security services and capabilities together that aim for attack mitigation and countermeasure techniques that are integrated into the overall secure SoC lifecycle. The design and integration of these secure enclaves need to achieve the highest assurance and certification of security, taking into consideration the intrinsic challenges of secure elements design and integration into the SoC lifecycle. To this end we perform a holistic study which comprises of two threads of activity: Vulnerability Analysis: We assess the security enclave’s (SE) ability to perform secure tests, SoC authentication among untrusted foundries, and OSAT environment. We also analyze the SE’s vulnerability to various threat scenarios such as information leakage, side channels, fault injection, etc. along with attacks such as man in the middle, impersonation, and more. Countermeasure Developments: We develop innovative solutions to ensure SoC authentication, in the field using AMI infrastructure and secure boot. We develop security policies to ensure proper implementation of SE and incorporate tamper resiliency for in-field.
Technology Highlight
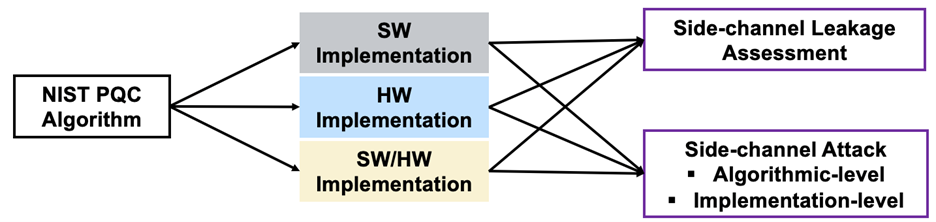
FICS Research Collaborates with NIST on Evaluating Side-Channel Attacks on Post-Quantum Cryptography
In 2016 the American National Institute of Standards and Technology (NIST) started a post-quantum cryptography (PQC) standardization process for key encapsulation mechanisms (KEM) and digital signature schemes. The competition began with 69 proper submissions in December 2017. As of July 22, 2020, the competition entered the third round with 7 finalist algorithms (4 KEM/Encryption and 3 Signature). The recent advance in the PQC field has gradually shifted from the theory to the implementation of the cryptosystem, especially on the hardware platforms. During the standardization process, it is necessary to validate the candidates’ implementation with secure countermeasures with regard to hardware vulnerability to side-channel attacks. In this work, FICS Research focuses on secure and efficient hardware implementations of three Lattice-based KEM finalists and analyze their vulnerability to power side-channel attacks in order to provide efficient countermeasures. Drs. Mark Tehranipoor, Farimah Farahmandi, Fahim Rahman, Jungmin Park, and Nalla Nachimuthu of FICS Research collaborate on this problem with NIST counterpart.
Accolades

Prof. Domenic Forte Awarded Yatauro Faculty Fellowship
Associate Professor and Director of the FICS Research SCAN Lab Dr. Domenic Forte has been awarded the Steven A. Yatauro Faculty Fellowship. The endowed fellowship was created to honor a faculty member who continues to inspire students and is attempting to solve society’s most challenging problems. The endowment will provide additional funding for the exploration of new and creative concepts in the lab.
2021 FICS Research TDC

2021 FICS Research TDC I
The first-ever FICS Research Technology Demo Conference (TDC) took place in March of this year. As we could not hold our annual conference in person due to the pandemic this spring, we devised the idea of taking the opportunity to showcase all of the hard work our students and faculty have still been putting in.
The three-day, all virtual, event featured demo presentations from FICS Research Ph.D. students and faculty on all of the new technologies, tools, and solutions they have been developing and perfecting over the past year. It also featured three keynote speakers and 2 invited speakers who featured their own work from academia, industry, and government. With well over 320 attendees, 6 generous sponsors, and 20+ new technology demonstrations, the event was a success! We remain ever grateful for our community’s sustained support, engagement, and continued interest in our research!
FICS Research TDC II
Save the date and keep an eye out for and save announcements coming your way soon about FICS Research TDC II, which is scheduled for September 14-15, 2021, and will feature new software-centered tools and technologies.
Now Hiring

Dr. Walden (Wally) Rhines Professorship in Fully Homomorphic Encryption (HFE) – Herbert Wertheim College of Engineering
The Herbert Wertheim College of Engineering at the University of Florida (UF) invites applications for a full-time, nine-month tenure track faculty position at the rank of Assistant/Associate/Full Professor in the Department of Electrical and Computer Engineering, or the Department of Computer & Information Sciences & Engineering (CISE). Candidates are sought whose research focuses on fully homomorphic encryption (FHE) and who are interested in collaborative research with the Florida Institute for Cybersecurity (FICS) Research, housed within the Herbert Wertheim College of Engineering.
Student Spotlight

Luis Vargas, Ph.D. Student & Research Assistant
“My research interest lies in the intersection between data science, cybersecurity, and disinformation. My focus is on better understanding the spread of fake news and the detections of information operations (disinformation campaigns). More precisely, I work in identifying the challenges that automatic detection mechanisms have in regards to their deployment in social media sites. My research work @ UF has covered many research fields ranging from cryptography, cellular security, to voice security but my main focus in on disinformation. Throughout my academic career, I also held multiple internship positions doing automotive research at Ford Motors (2014), aerospace research at NASA Ames Research Center (2014,2015), and disinformation research at FireEye (2019,2020). After graduation, I am excited to join the information industry to continue working in solving the disinformation problems we face today!”
Luis is currently working on a project titled “The Role of Spoken Language in the Detection of Fake News Articles.”
“Fake news has become one of the biggest problems that Twitter, and other social media sites, currently face. While many proposed solutions automatically detect when a fake news article is spreading or becoming “viral,” the detection mechanisms usually rely on learning the distinction between real and fake news articles by using datasets that heavily favor the English-speaking community. As such, it is unclear how well the distinctions learned from the English datasets encompass the real and fake behavior of news articles when considering the social media ecosystem as a whole. As the lead on this project, we explore how the spread of news articles differs based on the language that drives the conversation. As the lead for this project, I worked on all aspects of the modeling pipeline ranging from data collection, extracting diffusion networks from the tweet engagement of news articles, featurizing the network models to generate numerical representations of the diffusion of news articles, and analyzing the differences between Spanish and English diffusion.”

Major News

Farahmandi Receives $500K DARPA Grant to Enhance Chip Security, Speed Time to Market
ECE Assistant Professor and member of the Florida Institute for Cybersecurity (FICS) Research Farimah Farahmandi has been awarded a $500K grant from the Defense Advanced Research Projects Agency (DARPA) for her project, “Security-Aware High-Level Synthesis (SHINE).” The project, which simultaneously introduces enhanced security strategies into the chip manufacturing process while significantly shortening the time to market, comes at a time when there are significant global shortages and slowdowns in chip manufacturing.
Constraints
Global chip manufacturing exists in a market where the pressure to get new products into the market as quickly as possible is incredibly intense. Especially driven by Internet of Things (IoT) devices, fierce competition and frantic innovation mean that in order to survive, products must hit the market as quickly and securely as possible. The chips powering the devices often have a time-to-market of six months to a year, an eternity in today’s market. Unfortunately, the result is the well-documented problem that security considerations are often the first to be ditched—testing and verifying that the chips are in fact functioning securely with no potential confidentiality or integrity violations – are indeed time consuming and complex.
Secure by Construction
Research led by Dr. Farahmandi takes the novel approach of building the enhanced security into the design phase, removing the need to perform post-manufacture security testing and verification. This yields a safer chip that is “Secure by Construction,” yet is able to get to market more quickly. SHINE achieves this dual improvement by injecting a series of complex security rules to the high-level synthesis (HLS) tool that is used in the design phase. These rules—key protection, information isolation, and access controls—make the HLS tool security-aware, whereas it previously was optimized only for power efficiency, are, and functionality. SHINE shows great promise in reducing slowdowns in the chip design while creating a pathway for more secure chips and products.

Emerging Topics in Hardware Security – Mark Tehranipoor
This book provides an overview of emerging topics in the field of hardware security, such as artificial intelligence and quantum computing, and highlights how these technologies can be leveraged to secure hardware and assure electronics supply chains. The authors are experts in emerging technologies, traditional hardware design, and hardware security and trust. Readers will gain a comprehensive understanding of hardware security problems and how to overcome them through an efficient combination of conventional approaches and emerging technologies, enabling them to design secure, reliable, and trustworthy hardware.
Technology Highlight
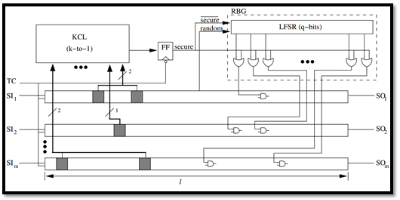
Test of Time Technology: Lock & Key or Logic Locking
Logic locking has received significant attention over the past decade or so. It’s an interesting technology to help protect IP from piracy and reverse engineering, Although it showed good promise for a while, it ran into major vulnerabilities to SAT and machine learning-related attacks. Indeed, more progress is needed to strengthen the solution against these attacks. The first-ever locking concept was developed by then a young professor, Mark Tehranipoor, to help protect IPs in a paper titled “A Low-Cost Solution for Protecting IPs Against Side-Channel Scan-Based Attacks,” In the 2006 IEEE VLSI Test Symposium (VTS’06). It’s a lock and key concept that, for the first time, uses locking gates to obfuscate the circuit and prevent access to scan. If the correct key is not applied, the circuit functions incorrectly. The concept has grown significantly since then. The Locking concept is now used for hardware metering, trojan prevention, and some even for software protection. Since the attacker is assumed to have access to the gate level netlist, the locking concept is susceptible to physical contactless probing attacks. More research is needed to address these concerns.
Accolades

Congrats to Andrew Stern, who has been selected as an Activate Fellow, a selective fellowship for propelling cutting-edge research into start-up companies.
FICS TDC II: Save the Date

FICS TDC II
The next FICS Technology Demo Conference will be held September 14-15, with a focus on software security. Attendees will hear about new advances in applied cryptography, mobile device and network security, trustworthy machine learning, and other topics, as well as invited talks from senior researchers at Samsung Research and Qualcomm.
Registration is now open – reserve your spot today!
General Registration
Sponsor Registration
To stay abreast of developing details for this event, join our listserv.
Hardware Assurance Survey

FICS Research at the University of Florida in collaboration with researchers from the Ohio State University are running a Hardware Assurance Survey aimed at identifying key areas of interest for future research, development, and collaborations between Government, Industry, and Academia.
The result of the survey will be shared with the public. Please help us collect this valuable information by participating in this 10-15 minutes survey. Participants will be entered in a drawing to win 1 of 5 $75 Amazon Gift cards. All answers will be kept strictly confidential.
Student Spotlight

Mir Tanjidur Rahman, Ph.D. Student & Research Assistant
I am Bangladeshi, raised in Dhaka, the capital of Bangladesh. Living in the country’s business center allowed me to meet people and make friends that have different beliefs, cultures, and mindsets. I received my B.S. and M.S. from the Bangladesh University of Engineering and Technology. I joined the University of Florida in 2017 as a Research Assistant under Dr. Navid Asadizanjani.
My primary research interests are VLSI and failure analysis. These interests turn my research goal into establishing assurance and security in electronic devices and systems. Currently, my research focus is on chip backside security against physical attacks, developing computer-aided design tools for probing attack solutions, and packaging security. I am also interested in emerging topics including memory security assessment, new probing, and fault-injection modalities exploration.
I am involved in multiple projects, and I enjoyed working on each of them. Security assessment of logic locking against optical attacks is one of my “close to heart” projects. Logic locking is a key-based hardware IP locking mechanism. Over the year, the locking key is considered to be secured under the assumption that tamper-proof memory protects the key. We showed the fallacy of this assumption with optical probing. These days I am excited about the ONR-funded “SAIPA: Security Aware Interposer Design for Heterogeneous Packaging” project. Developing security solutions and computer-aided design methods for 2.5D packaging is the goal of this project.
In FICS, I always had the pleasure to collaborate with some of the most visionary, brilliant, and dedicated minds in the security field. Thanks to all my collaborators, we’ve had the privilege of being able to output several conference papers, journal papers, and patents. My latest research, “Concealing-Gate: CONCEALING-Gate: Optical Contactless Probing Resilient Design,” is published in ACM JETC, 2021. Recently, we managed to publish a book titled “Physical Assurance For Electronic Devices and Systems.” Without the help of my colleagues and collaborators, it would remain a dream too difficult to even dream about.
Security and privacy will always remain a significant concern at both individual and state levels. So, as a security researcher, it’s my responsibility to make sure the show must go on for technology advancement. I try to fulfill that duty by finding vulnerabilities and innovative solutions in emerging systems and applications and establishing trust in technologies that become ubiquitous in our daily lives.
I also involve myself in mentoring activities for security researchers. I helped them to realize their potential and train new skills. It’s always enjoyable to prepare young minds for new challenges and watch their dreams grow. After all, deep inside I am always afraid of letting my dream go like:
“I turned to look, but it was gone
I cannot put my finger on it now
The child is grown, the dream is gone.”
-Comfortably Numb, The Wall, Pink Floyd

Major News

Dr. Asadi (FICS) and Dr. Need (MSE) Partner on $270k SRC Project
Our proposal presents a first-ever methodology to enable hardware reconfiguration of interconnects and I/O inside the package even after the chip is fabricated. The prime feature of this novel technique is the trusted designer or IP owner will have the flexibility of reconfiguring and obfuscating the golden hardware design throughout the supply chain. Unlike the traditional obfuscation methods, here, the hardware connections will be reconfigured and changed when the chip is functional. In other words, there will be two states of the hardware configuration for the interconnects and I/O’s – ON-state and OFF-state design. In the OFF-state design, the configuration will be random, and this random design will be used for fabrication, testing, and distribution. If any adversaries in the supply chain get access to this OFF-state design or chip fabricated using this design will not be functional. To bring the device into the ON-state, a separate boot code will be provided by the IP designer upon verification and authentication. In the ON-state, the hardware of the I/O’s will be reconfigured to the golden design and this design will be retained until the chip is operational. After the usage, the chip will reset back to the OFF-state, and the connections will be random again. Therefore, adversaries will not be able to extract the actual design of the package, as to see the golden-designed configuration, the device needs to be functional and should have the boot code provided by the IP owners upon authentication.
Technology Highlight
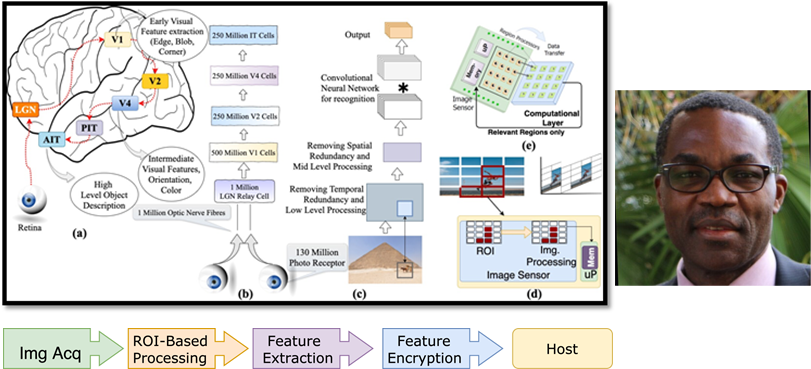
Bio-Inspired Secure Vision Sensor: Toward a Reconfigurable Hardware Modeling of the Hierarchical Processing in the Brain
Biological vision systems (BVS) always show a plausible and optimal way for video processing in the field of computer vision. This work leverages the concepts of BVS to perform event-based pixel-parallel near-sensor processing for enabling sensor-level scene understanding with low power. With the increasing size of images, the sequential nature of data transfer and processing is becoming a bottleneck for high-speed processing. To tackle the complexity of future image processing systems, especially at the edge, this research applies brain-oriented methods to devise a hierarchical and pixel-parallel architecture for performance and low-power processing at the edge. BVS has parallel pathways in the hierarchy, where irrelevant information in the stream is filtered out to reduce the amount of data for higher processing. This concept is leveraged to identify important regions. It allows computationally expensive operations to be performed only on a reduced amount of data, thus minimizing power, area, and latency. The data reduction scheme is used for a deep learning module at the end of the chain, specifically optimized to dynamically adapt to data size. A corresponding learning flow has been designed to take advantage of the redundancy in data and reduce training time. Security is integrated within the sensor through end-to-end encryption and decryption. FPGA prototyping and ASIC simulation prototype design have demonstrated substantial speedup, power, and resource reduction of the proposed architecture.
Student Spotlight

Dr. Sumaiya (Jyoti) Shomaji, PhD Graduate
Congrats to Dr. Sumaiya Shomaji who successfully defended her PhD dissertation and will soon join the Computer Science faculty at Texas Tech as an assistant professor!

Dr. Mir Tanjidur (Tanjid) Rahman, PhD Graduate
Congrats to Dr. Mir Tanjidur Rahman who successfully defended his Ph.D. dissertation and will be joining Intel as a Sr. Server Debug Engineer in Hudson, MA!

Dr. Andrew Stern, PhD Graduate
Congrats to Dr. Andrew Stern who successfully defended his Ph.D. dissertation and is now Founder & CEO of Coremeleon and an Activate Boston Fellow funded by DARPA!

Dr. Ulbert “Joey” Botero, PhD Graduate
Congrats to Dr. Ulbert Botero who successfully defended his Ph.D. dissertation and will now use his time to travel and look for research and development positions in industry or national research laboratories.

Dr. Didem Pehlivanoglu, Postdoc
Congrats to Dr. Didem Pehlivanoglu on receiving the APA Division 20 Postdoctoral Research Award for the presentation of research examining Older Adults Ability to Evaluate Fake News During the Pandemic.

Luke Bauer, PhD Student & Research Assistant
I am a 4th year PhD student researching machine learning in cybersecurity. I attended Duke University for my undergraduate degree, and now work in the FICS lab under Prof. Vincent Bindschaedler. While I have done work on privacy, membership inference, and self-driving cars, my research focus within machine learning is on generative models and steganography. Generative models are a type of ML model that are able to create new samples similar to the data they were trained on. These models have seen massive improvements in the last few years and have a wide range of uses, including deepfakes, adversarial examples, private synthetic data, and steganography. The majority of my work within these topics has been on steganography, which is the study of hiding a secret message within something that is not secret. The most common way to achieve this is to embed a secret message within an image by adding perturbation invisible to the human eye to a cover image, but secret messages have also been hidden in audio, video, and even other text files. Steganography is one of the safest ways to get messages out of places with extreme censorship since the media the message is hidden in looks like innocent internet traffic and often can only be detected with other specialized ML models.
One of the projects I am currently working on studies how generative models can be used to generate innocent looking social media text posts, where the words chosen contain information the receiver can use to recreate a secret message. We also study the challenges that arise when users use these messages to safely communicate over popular sites. It is titled “Covert Message Passing over Public Internet Platforms Using Model-Based Format-Transforming Encryption,” and following is the abstract.
“We introduce a new type of format-transforming encryption where the format of ciphertexts is implicitly encoded within a machine-learned generative model. Around this primitive, we build a system for covert messaging over large, public internet platforms (e.g., Twitter). Loosely, our system composes an authenticated encryption scheme, with a method for encoding random ciphertext bits into samples from the generative model’s family of seed-indexed token-distributions. By fixing a deployment scenario, we are forced to consider system-level and algorithmic solutions to real challenges such as receiver-side parsing ambiguities, and the low information-carrying capacity of actual token-distributions that were elided in prior work. We use GPT-2 as our generative model, so that our system cryptographically transforms plaintext bitstrings into natural-language covertexts suitable for posting to public platforms. We consider adversaries with full view of the internet platform’s content, whose goal is to surface posts that are using our system for covert messaging. We carry out a suite of experiments to provide heuristic evidence of security, and to explore tradeoffs between operational efficiency and detectability.”

Major News

UF Researchers Awarded $1.1M Grant by National Institute of Health on AI-Powered Medical Research
A multi-departmental team from the University of Florida, Dr. Shigang Chen, Dr. Samuel Wu, Dr. David Vaillancourt, and Dr. Kejun Huang, was recently rewarded a $1,172,041 grant from the National Institute of Health on AI-powered medical research, specifically for Parkinson’s disease.
The project title is SCH: Enabling Data Outsourcing and Sharing for AI-powered Parkinson’s Research. The grant will be enacted from 09/03/2021 to 05/31/2025.
“Artificial intelligence holds the promise of transforming data-driven biomedical research and computational health informatics for more accurate diagnosis and better treatment at lower cost. In the meantime, modern digital and mobile technologies make it much easier to collect information from patients in large scale. While “big” medical data offers unprecedented opportunities of building deep-learning artificial neural network (ANN) models to advance the research of complex diseases such as Parkinson’s disease (PD), it also presents unique challenges to patient data privacy. The task of training and continuously refining ANN models with data from tens of thousands of patients, each with numerous attributes and images, is computation-intensive and time-consuming.“
The full abstract for SCH: Enabling Data Outsourcing and Sharing for AI-powered Parkinson’s Research can be found here on the FICS Research website.
Accolade

FICS Research Team Wins Best Screenplay Award at 2021 IEEE Security & Privacy Conference
CISE faculty members Dr. Tom Shrimpton and Dr. Patrick Traynor, along with CISE Ph.D. students Hadi Abdullah, Muhammad Sajidur Rahman, Washington Garcia, Kevin Warren, and Anurag Swarnim Yadav won the Best Screenplay Award at the 2021 IEEE Security and Privacy Conference for their paper, “Hear ‘No Evil’, See ‘Kenansville’: Efficient and Transferable Black-Box Attacks on Speech Recognition and Voice Identification Systems.”
Computer scientists are not typically known for writing screenplays—in this case, researchers created a script and visualization of the particular research problem discussed in their paper. The video below includes dialogue and the written basis for the project.
Watch the MEST Interview with Dr. Wally Rhines

Dr. Wally Rhines, CEO of Cornami, Former CEO of Mentor Graphics
Wally Rhines is widely recognized as an expert in business value creation and technology for the semiconductor and electronic design automation (EDA) industries. Dr. Rhines was CEO of Mentor Graphics (a “Big Three” EDA company with $1.3B+ revenue) for 24 years, has served on the boards of five public companies, managed the semiconductor business of Texas Instruments (TI), and is a spokesperson, writer and highly-sought-after speaker for the high-tech industry delivering more than twenty keynotes per year. Dr. Rhines currently serves as President and CEO of Cornami, Inc., consults for investors, corporations and the U.S. government on strategic directions, value creation and technology and serves on public and private boards.
Student Spotlight

Dr. Luis Vargas, FICS Research Ph.D. Graduate
Congrats to FICS Research’s recent Ph.D. graduate, Dr. Luis Vargas. Dr. Vargas was supervised by Dr. Patrick Traynor from CISE. He will be moving into a position as a Data Scientist at Alethea Group, a startup that focuses on identifying and mitigating online disinformation.

Md Rafid Muttaki, Ph.D. Student & Research Assistant
“I am a 3rd year Ph.D. student at the ECE Department, University of Florida. I am working at the Florida Institute for Cybersecurity (FICS) Research under Dr. Farahmandi’s supervision on several projects to ensure design security at both digital and analog domains. I received my bachelor’s degree from BUET in 2017 and worked in a local semiconductor company in Bangladesh until 2019. In FICS, we have been developing an IP protection technique using High-Level Synthesis (HLS). Although HLS provides an excellent platform for designers to develop complex designs in lesser time and effort, there are underlying security vulnerabilities relating to the HLS process that we intend to address and rectify in another project. We are working on a universal sensor to detect physical attacks (i.e., Fault Injection, Glitch) directed to a chip in the analog domain. Also, we are developing an obfuscation technique to protect pure analog and mixed-signal designs.”
Upcoming MEST Interview with Serge Leef, Program Manager at DARPA

Program Manager, DARPA
September 29, 2021 @ 12 p.m. EST
Check Out Our YouTube Channel!
We have recently uploaded several lab demo videos to our FICS Research channel! Feel free to check them out and look forward to more videos soon.
https://www.youtube.com/channel/UCRO_5xSMoVBMQwF_PY0zxwQ/videos

Major News

Dr. Asadi to Serve As Program Chair For 2021 IEEE PAINE Conference
ECE Assistant Professor Dr. Navid Asadi will be serving as the program chair for the well-regarded 2021 IEEE PAINE Conference, to be held Nov. 30–Dec. 2, hosted virtually from Washington, D.C.
The PAINE Conference provides a unique venue to researchers and practitioners from academia, industry, and government to have productive dialog concerning the physical inspection of electronics. This area has grown significantly over the past decade (there were more than 300 attendees in 2020) and is becoming a major focus for the chip designers, original equipment manufacturers, and system developers. The complex long life of the electronic devices coupled with their diverse applications are making them increasingly vulnerable to various forms of threats and inspection. Large industry and government efforts have been put in place across the globe to address related supply chain security problems to offer solutions, training and services. The number of programs introduced by US government have increased over the years to analyze and develop relevant solutions. Although much focus is given to digital domain, physical assurance and inspection of electronics as well as physical fingerprinting based on analog parameters are rapidly providing opportunities for unique countermeasures.
The PAINE Conference was founded by Dr. Asadi and Dr. Mark Tehranipoor in 2018 as a collocated workshop with the DAC Conference, but quickly became a free-standing, independent conference. Tehranipoor is serving as the general chair for the 2021 conference.
The PAINE 2021 program promises scores of interesting talks by researchers and program managers from entities such as: New York University, Purdue University, Intel, DARPA, the US Navy, Facebook, AWS, NIST, and SRC. A full list of speakers is available here.
Dr. Jay Lewis’ MEST Interview + The Future of Electronics Packaging Security Panel
Rewatch Dr. Jay Lewis’, Partner, Silicon Projects at Microsoft, MEST interview with Dr. Mark Tehranipoor, Director of FICS Research, on our FICS Research YouTube channel now! The discussion focused on microelectronics security, including the problem domain.
If you missed our first-ever MEST Panel, make sure to watch it right here! The panel features David Kehlet, John Oakley, Jeffrey Demmin, and John Allgair. Watch the discussion and viewpoints on new trends in the semiconductor industry and OSAT toward advanced integration and heterogeneous packaging (2.5D, 3D) that offers unique challenges and security concerns.
Hardware Assurance Survey Results

Hardware Assurance Survey Results
FICS Research at the University of Florida in collaboration with researchers from the Ohio State University ran a Hardware Assurance Survey aimed at identifying key areas of interest for future research, development, and collaborations between Government, Industry, and Academia.
The results are interesting, and if you would like to view more, click on the links above to view our full results of the survey.
- We had a total of 176 participants ranging from Government and DIB to Industry and Education leaders.
- SoC vulnerability assessment against info leakage, Trojan, side-channel leakage, fault injection, and more is rated as the highest priority in the topic of Hardware Security and Trust.
- Open-source CAD tools for security verification is rated the lowest priority in the topic of CAD for Assurance.
- Industry leaders chose System-level risk and vulnerability analysis, Risk analysis considering hardware-software issues as the highest priority under the topic of Hardware Security and Trust.
FICS Research Outreach
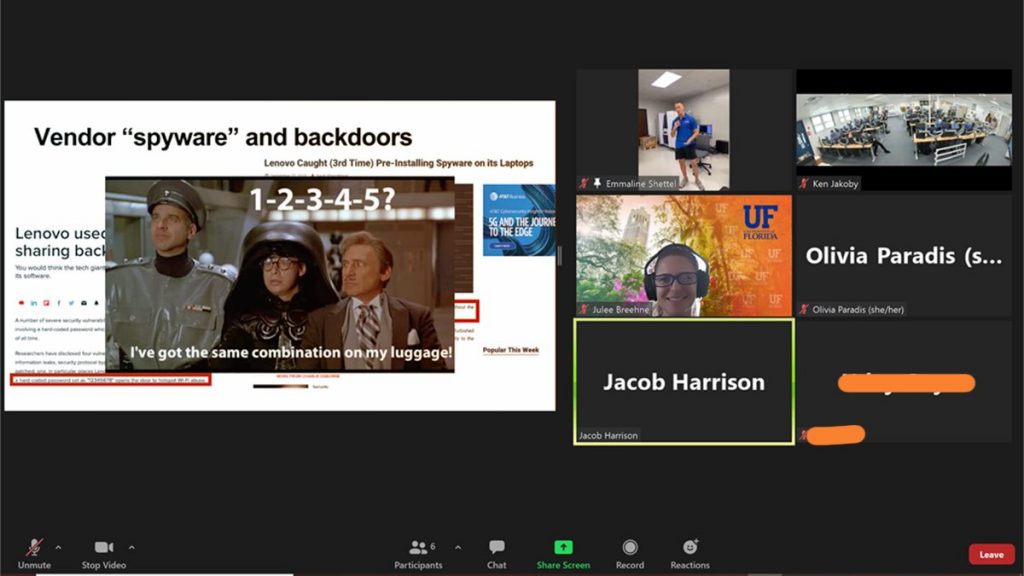
FICS Research Lab Tour with North Port HS Students
CyberGatorz from FICS Research put on a lab tour for North Port High School Students. The lab tour was led by 4 Ph.D. students, Olivia Paradis, Jacob Harrison, Nathan Jessurun, and John True, discussing cybersecurity and graduate school. The students asked great questions about biometrics and even environmental engineering.
Thanks to our Ph.D. students at FICS Research for sharing their knowledge and experience with high school students that will be entering college soon!
Accolade

Rabin Acharya, best poster winner in “Poster Track 1 – AI Architectures and Algorithms” at the 2021 IBM IEEE AI Compute Symposium
Rabin Acharya, a Ph.D. student at FICS Research under Dr. Domenic Forte, won best poster winner at the 2021 IBM IEEE AI Computer Symposium. The title of his poster is “InfoNEAT: Information theoretic-based Neuroevolution of Augmenting Topologies for Developing Compact and Quantized Neural Networks,” and this was collaborative work with former postdoc Dr. Fatemeh Ganji. The bottom of this link shows the winners from each track: https://www.zurich.ibm.com/thinklab/AIcomputesymposium.html
Student Spotlight

David Koblah, Ph.D. Student and Research Assistant
“This is my 3rd year at the University of Florida. I came to the Florida Institute for Cybersecurity (FICS) Research in 2018 under the Summer Undergraduate Research at Florida (SURF) program. Dr. Domenic Forte was my faculty mentor, and Joey (now Dr. Ulbert Botero) provided guidance as a senior Ph.D. Student. I returned to FICS Research in 2019 after receiving my bachelor’s degree in Computer Engineering from Texas Tech University. Dr. Forte became my supervisor, and my work under him has been very diverse. Most of the work focuses on using Machine Learning and Artificial Intelligence to enhance Printed Circuit Board (PCB) Reverse Engineering and Integrated Circuit (IC) Design. For PCB Reverse Engineering, we are using Deep Learning and Computer Vision to automate the detection of connections on a PCB x-ray tomography. X-ray allows us to extract individual layers without destroying the PCB. For ICs, we are attempting to enhance device security at various stages while improving the overall design. One of our projects focuses on using evolutionary algorithms to minimize designs at the gate level and optimize them. We hope to further explore the latter need in the coming years.

