
Events
2020 FICS Research Annual Conference on Cybersecurity @ University of Florida



MEST Webinars

Major News

Hadi Abdullah placed second in the Applied Research competition at NYU’s CSAW Competition for his paper titled “Practical Hidden Voice Attacks against Speech and Speaker Recognition Systems.” And team G8rs, consisting of Grant Hernandez, Hunter Searle and Hadi Abdullah, placed third in the Security Quiz Bowl.
Technology Highlight
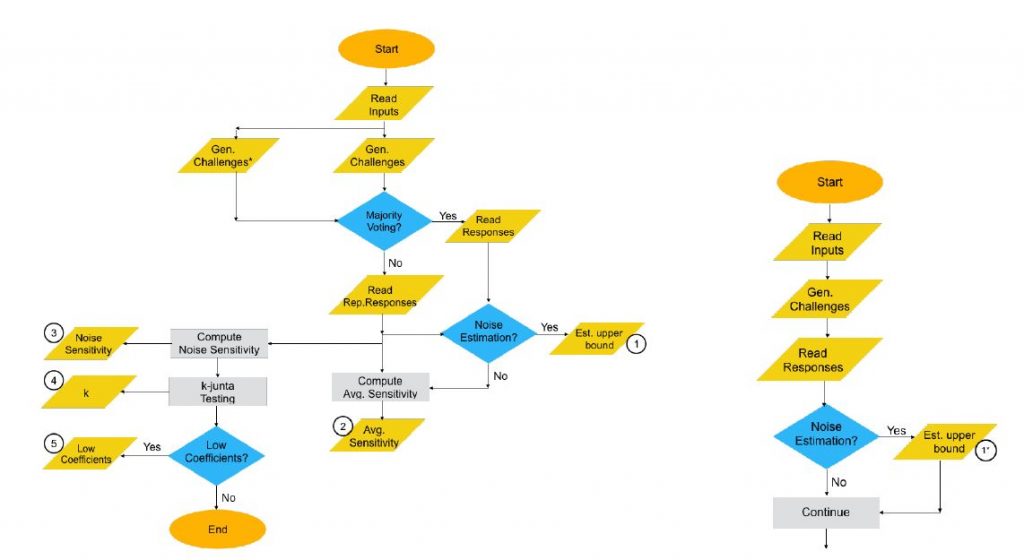
PUFmeter: A New Toolbox to Assess the Robustness of PUF’s to Machine Learning Attacks
A physically unclonable function (PUF) can be thought of as either a device fingerprint for secure authentication or as a source of entropy in secure key generation scenarios. Although standard metrics for estimating PUF quality exist, the most common approaches for measuring resistance to machine learning (ML) attacks are empirical. PUFmeter addresses this by introducing a toolbox, composed of not only provable ML algorithms to assess the security of PUF, but also modules useful to evaluate other robustness-related properties of PUFs and pre-process the CRP data set for this purpose.
Fatemeh Ganhi, Domenic Forte, and Jean-Pierre Seifert
Faculty Highlight

Congratulations to Dr. Farahmandi who just published a new book called, “System-on-Chip Security: Validation and Verification”!
Student Spotlight

Sumaiya Shomaji won first prize in the loT Technology poster session at the Nelms loT Conference!
Title: Hierarchical Bloom Filter Framework for Security, Space-Efficacy, and Rapid Query Handling in Biometric Systems.

Technology Highlight
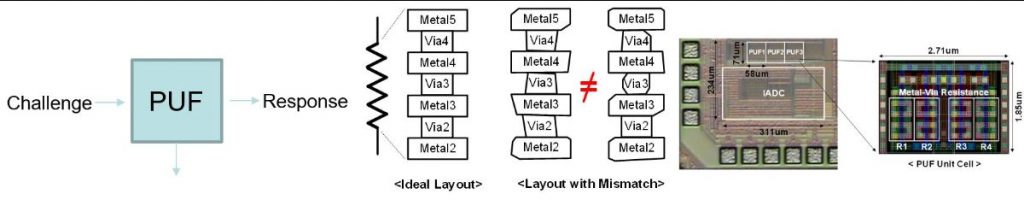
| “…A physically unclonable function (PUF) leveraging the parasitic resistance created by the metal-via interconnection as entropy source is proposed in this paper. Metals 2 through 6 of a 65nm process is used to create the necessary parasitic resistance. Instead of using additional stabilization techniques, an incremental analog-to-digital converter is implemented to precisely measure the voltage difference between two branches consisting of the metal-via interconnection based parasitic resistances….” Read More |
Student Highlight

Nusrat Farzana Dipu was invited to attend CRA-WP, a computer research association focused on increasing the success and participation of underrepresented groups in computing research.
Faculty Highlight
Dr. Patrick Trayor gave a keynote address at the Annual Computer Security Applications Conference (ACSAC) Conference about his work with FICS an how to transition into real world practice.


Major AI partnership with NVIDIA: Dr. Damon Woodard of FICS Research Will Lead Training
The University of Florida announced a public-private partnership with NVIDIA that will catapult UF’s research strength to address some of the world’s most formidable challenges, create unprecedented access to AI training and tools for underrepresented communities, and build momentum for transforming the future of the workforce. FICS faculty member, Dr. Damon Woodard, will be leading the training as the Director of AI Partnerships.

The Edaptive Computing Inc. Transition Center (ECI-TC) Website Has Been Launched
The Edaptive Computing Inc. Transition Center (ECI-TC) is strongly committed to diversity, equity, and inclusion with a focus on domestic students.
Click here for a complete list of students
Click here for projects
Dr. Domenic Forte Hosted IEEE HOST Online Panel
Dr. Domenic Forte hosted an IEEE HOST online panel entitled “How Can Hardware Security contribute to the Fight Against COVID-19 and to Post-Pandemic Life?”. The new normal and upcoming practices/technologies have opened up the door to unfamiliar security and privacy issues. During this webinar, the moderator and panelists discussed some of the risks, opportunities, and possible roadmaps for researchers in the field of hardware security to address them. The webinar was successful with 409 registrants and 177 live attendees. The panel video will be archived by IEEE Computer Society for viewing.
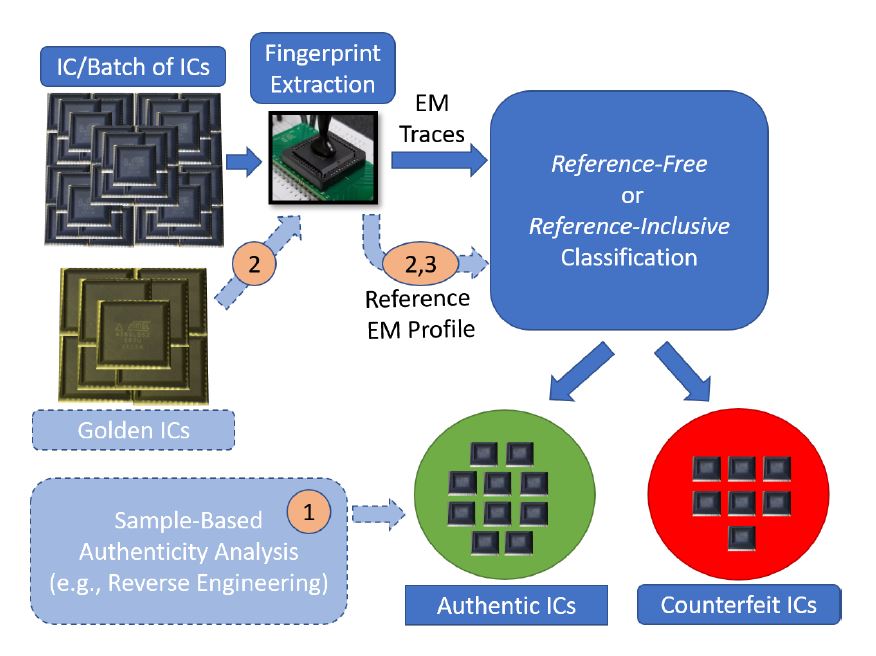
EMFORCED: EM Based Fingerprinting
Electronics supply chain vulnerabilities have broadened in scope over the past two decades. With nearly all IC design companies relinquishing their fabrication, packaging, and test facilities, they are forced to rely upon companies from around the world to produce their ICs. This dependence leaves the electronics supply chain open to counterfeiting activities. Th EMFORCED project develops electromagnetics-based fingerprinting framework to detect suspect ICs. Read article here.

CyberGatorz Win Fourth Place in Collegiate 2020 Capture-the-Flag
FICS Research’s student group, CyberGatorz, (comprised of Nitin Pundir, Jacob Harrison, Nidish Vashistha, Dhwani Mehta, Avinash Ayalasomayajula, and Tao Zhang) were tasked with the challenge of building a secure audio digital rights management (DRM) module for the next generation of multimedia players. CyberGatorz were then awarded for fourth for most points overall, combined from capturing and defending flags as well as documentation and write-up of a design feature and an advanced attack.

Welcome to FICS Research, Dr. Sara Rampazzi
Dr. Sara Rampazzi is an incoming Assistant Professor in the Department of Computer and Information Science and Engineering (CISE) at the University of Florida. Her research areas include cyber-physical systems security, embedded systems design, modeling, and simulation with applications in Healthcare, Automotive, and the Internet of Things. Dr. Rampazzi’s work focuses on investigating security risks and developing hardware and software defense strategies against hardware-based and physic-based attacks.

FICS Student Wins the GEM Fellowship
FICS Research student, Princess Lyons, whose research interest focus on machine learning methods for object detection and is advised by Dr. Woodard, was awarded the GEM Fellowship for the upcoming school year and has been completing an industry internship as a Data Scientist with Lam Research Corporation in Fremont, CA, one of the world’s leading semiconductor companies. The mission of The National GEM Consortium is to enhance the value of the nation’s human capital by increasing the participation of underrepresented groups.


The Edaptive Computing Inc. Transition Center (ECI-TC) Website Has Been Launched
The Edaptive Computing Inc. Transition Center (ECI-TC) is strongly committed to diversity, equity, and inclusion with a focus on domestic students.
Click here for a complete list of students
Click here for projects
FICS Research Faculty, Dr. Christophe Bobda, recieved a NSF Grant
This project aims at addressing the problem of multi-tenancy in FPGA-accelerated clouds and datacenters by providing the architecture and mechanisms for the efficient sharing of FPGA devices among multiple users. Specifically, the PI will design and implement 1) hardware and software virtualization technologies for the integration of segments of the same hardware into cloud hypervisors, 2) isolation framework based on the NSA-developed Flux Advanced Security Kernel (FLASK) to extend domain separation from software threads and virtual machines down to provisioned hardware accelerators, and 3) temporal and spatial management approaches of the hardware resources, from the admission control to the execution on the FPGA device.

FICS Research Conference Update

FICS Research Director, Dr. Mark Tehranipoor’s, Technology Was Recognized the IEEE Spectrum Article
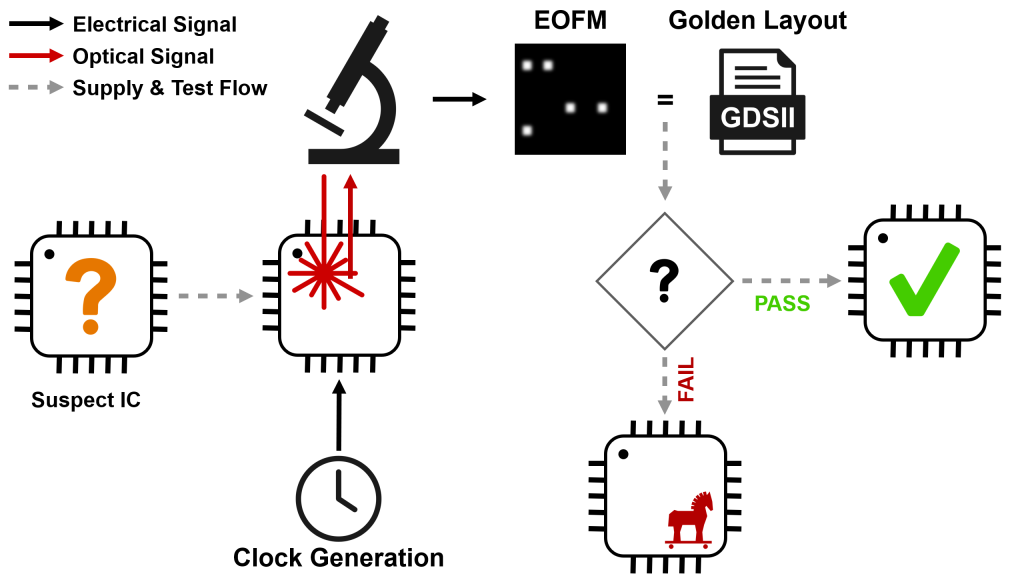
A recent article in IEEE Spectrum entitled, “Three Ways to Hack a Printed Circuit Board”, features technology developed by FICS Research Director, Dr. Mark Tehranipoor. The technology referenced involves a system which uses optical scans, microscopy, X-ray tomography, and artificial intelligence to compare a PCB and its components with the intended design. Read more about it here.

Student Spotlight: Jasmine Bowers
FICS Research student, Jasmine Bowers, is the first African American to receive her PhD in computer science at the University of Florida. Jasmine’s research interests are security and privacy in wireless and mobile networks. Congratulations, Dr. Jasmine Bowers!
The MEST Center is Hiring
The MEST Center is hiring a Research Assistant Scientist. The chosen candidate will lead workshops, webinars, and other training sessions on a variety of topics related to hardware and microelectronics security and assurance for its new Microelectronics Security Training (MEST) Center. Apply here!


Congratulations
to Dr. Tehranipoor for both receiving the Invention of the Year award as well as being recognized by DSP as one of the top (4) PIs in Awarded Funding for 2020.

Dr. Damon Woodard’s, Artificial Intelligence Partnership with NVIDIA
Dr. Damon Woodard, resident AI expert at FICS Research, will be partnering with NVIDIA to provide training in AI in a new public-private relationship that will catapult UF’s research strength to address some of the world’s most formidable challenges, create unprecedented access to AI training and tools for underrepresented communities, and build momentum for transforming the future of the workforce. Dr. Woodard is currently working on multiple problems that involve the use of artificial intelligence to solve problems related to national security.
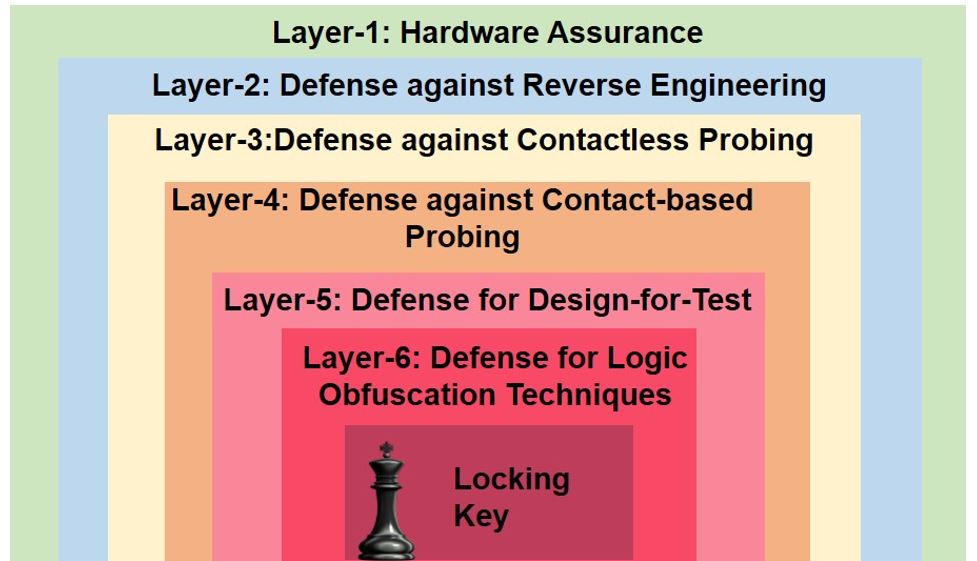
Key is Left Under the Mat: On the Inappropriate Security Assumption of Logic Locking Schemes
The supply chain of integrated circuits (ICs) has shifted from vertical to horizontal model over the past two decades. In the horizontal model, different chip manufacturing processes, like intellectual property (IP) design, fabrication, and design-for-test (DFT) structure insertion, are outsourced to more sophisticated offshore fabrication facilities. With many entities involved in the supply chain located across the globe, original IP manufacturers and original component manufacturers have faced IP piracy, overproduction, and cloning.
Read the full paper here.

Faculty Spotlight: Dr. Fahim Rahman
Dr. Rahman’s research delves into blockchain-enabled schemes for establishing trusted electronics supply chain allowing in-field deployment, computer-aided design methods for anti-piracy solutions targeting critical electronic IPs, and development of secure firmware for resource-constrained/IoT devices. The primary motivation behind his research is to establish assurance and security in electronic devices and systems from design to resign.
Learn more about Dr. Rahman and his background.

Alumni Spotlight: Sreeja Chowdhury
Sreeja Chowdhury was a FICS Research student who now works in the industry at Ansys San Jose. Sreeja recently joined as an Applications Engineer in Ansys San Jose. Ansys specializes in power analysis, EM analysis, side channel analysis tools. Sreeja will miss working with the Professors and peers at FICS Research the most. She will also miss being in the FICS scan lab and brainstorming.

Student Spotlight: Ashley Tramble
Ashley Tramble is a current FICS Research student who also works a Technical Fellow at the Kansas City National Security Campus managed and operated by Honeywell FM&T.
“FICS Research gave me resources to dive deeper into microelectronics. I started with the desire to learn how to fabricate ICs, but since then my interests have grown. Also, I have been able to become familiar with trending topics in electrical and computer engineering.”
The MEST Center is Hiring
The MEST Center is hiring a Research Assistant Scientist. The chosen candidate will lead workshops, webinars, and other training sessions on a variety of topics related to hardware and microelectronics security and assurance for its new Microelectronics Security Training (MEST) Center. Apply here!


FICS Research Gains Sponsrship from FDLOE
Dr. Mark Tehranipoor and his team at UF’s FICS Research created an innovative national training program entitled the Microelectronics Security Training (MEST) Center whose sole mission to make current and future technologies more secure. This program was developed in close collaboration with Dr. Waleed Kahlil at the Ohio State University. This innovation is unique among other recipients of a UF Innovate’s Invention of the Year Award in that it’s not a new idea or technology in the traditional sense, but a platform — a holistic training program anchored by the MEST Center, aimed at detecting and preventing security vulnerabilities in hardware and design.

2021 FICS Research Technology Demo Conference
Launched on Nov. 19, 2020, this project supported by the Air Force Research Laboratory (AFRL) will develop tools, methodologies, metrics, test vehicles, and more to help address the concerns on trusted microelectronics.

Dr. Wally Rhines to Serve as FICS Research Advisory Board Chair
Over the past 10 years, the NSF sponsored Trust-Hub has received million + page impressions and tens of thousands of visitors. Our “Benchmarks” and “CAD for Security Tools” remain the most popular items visited over the past several years.
Additionally, Phase III is quite focused on the concept of CAD for SoC Security, an effort Trust-Hub initially started a few years ago. Such solutions are necessary to making hardware security solutions available to the entire community (academia, industry, and government).
Faculty Highlight:
Shigang Chen
FICS Research’s Dr. Domenic Forte and PhD student, Sarah Amir, just posted a tool on Trust-hub called Synthetic Circuit Benchmark Generator. This is a framework that generates synthetic benchmarks optimized to have maximum variation from the reference benchmarks. It utilizes linear optimization to generate an endless number of synthetic combinational benchmarks that are adaptable to user input constraints and divergent in quantifiable structural features from input reference benchmarks. This framework offers customization for generating richer and more challenging benchmarks for data-driven hardware security.
View tool here.

Edaptive Computing Inc. Transition Center (ECI-TC) Now Hiring
The PAINE Conference provides a unique venue for all researchers and practitioners from academia, industry, and government to have productive dialogue on the broad topic of hardware security and trust.
Register here.
Technology Highlight:
TrustGuard: Runtime Anomaly Detection in IoT Devices
PIs: Farimah Farahmandi, Jungmin Park and Mark Tehranipoor
With the advent of the Internet of Things (IoT), embedded devices, and networked high-performance computation platforms, many different types of cyberattacks such as malware, ransomware, distributed denial-of-service (DDoS), etc., have become a significant concern. All network-connected devices are susceptible to such cyber and hardware attacks. Since low-cost loT devices have limited resources, such as low processing power, and memory capability, deploying sophisticated defense mechanisms is extremely difficult and financially infeasible, which makes them attractive targets to adversaries. It is with no doubt that successful cyberattacks can lead to serious economic loss, infrastructural damage, or loss of life.
Thwarting the threats and vulnerabilities against cyberattacks requires lasting attention. In particular, runtime monitoring of computing devices is highly necessary to detect malware, unauthorized access, and illegitimate controls and applications. Such monitoring techniques can be either software-based and hardware-based. The software-based method mostly performs control-flow integrity (CFI) assessment which can monitor unexpected changes by a malicious code by analyzing the runtime control-flow graph (CFG). However, such software-based methods have disadvantages of performance degradation and unavailability to devices with resource-constrained architecture.
On the other hand, hardware-based methods usually use embedded and/or independent trusted hardware to observe the behavior of a program running on the device under a monitor. Hardware-based CFI architecture integrates hardware monitors into processor’s pipeline stages or hardware debug interface such as JTAG or scan chain is used to validate CFI at runtime. Hardware-based detection methods require a smaller overhead for resource and latency compared to the software-based counterparts. Recently, researchers have paid more attention to hardware-based methods that leverage side-channel leakages such as power consumption and EM. The side-channel information can also be leveraged for analyzing the status of a computing system at runtime.
To monitor firmware integrity in IoT edge devices by leveraging power side-channel information, FICS with the Analog Device Inc. team will research and develop ADI SW IP that enables ADI (Linear) Power Supplies to add security monitoring services for any embedded devices.This IP could monitor and detect if the edge device is compromised and running rogue firmware/software by analyzing the side channel signature in Figure 1.

Student Spotlight: Olivia Paradis
Olivia Paradis is a current FICS Research student and a Research Assistant under Dr. Navid Asadi. Olivia’s primary research interests are image processing, computer vision, and machine learning. “Applications I am interested in include, but are not limited to: hardware assurance, medical diagnostics, mobility-enhancing technologies, and biometrics.”
Read more about Olivia’s current projects and achievements here.

Congratulations to Prof. Prabhat Mishra, a new IEEE Fellow Member at FICS Research!
Prabhat Mishra is a Professor in the Department of Computer and Information Science and Engineering at the University of Florida. His research has been recognized by several awards including the NSF CAREER Award, IBM Faculty Award, three Best Paper Awards, and EDAA Outstanding Dissertation Award. Prof. Mishra is an ACM Distinguished Scientist and a Senior Member of IEEE.